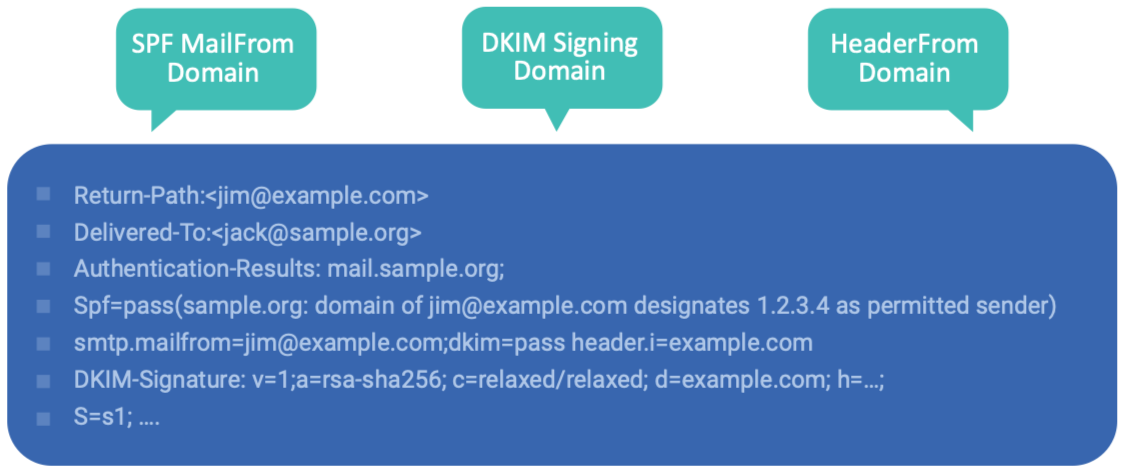
Strict alignment requires that domains in both the From: header and Return Path/”d=” DKIM field be a 100% match.
Relaxed alignment is more, well, relaxed in with its requirements. Even subdomains are allowed, as long as they’re under the same organizational domain (the From: domain).
DMARC alignment specifically addresses the limitations of SPF by ensuring that the From: and Return Path domains match, preventing attackers from trying to use different domains for each.
It also solves the loophole that can be used to exploit DKIM by requiring that the From: header also matches the domain given in the DKIM signature, removing the chances of someone forwarding the email with additional header fields.